Social Engineering Techniques and Security Countermeasures: A Comprehensive Guide

4 out of 5
| Language | : | English |
| File size | : | 3451 KB |
| Text-to-Speech | : | Enabled |
| Screen Reader | : | Supported |
| Enhanced typesetting | : | Enabled |
| Word Wise | : | Enabled |
| Print length | : | 264 pages |
Social engineering is a type of cyberattack that relies on human interaction to trick victims into giving up sensitive information or access to systems. Social engineers use a variety of techniques to build trust and rapport with their targets, making them more likely to comply with their requests.
Social Engineering Techniques
There are many different social engineering techniques, but some of the most common include:
- Phishing: Phishing emails are designed to look like they come from a legitimate source, such as a bank or government agency. They often contain links to malicious websites that can steal your personal information or infect your computer with malware.
- Spear phishing: Spear phishing emails are targeted at specific individuals or organizations. They are often more personalized than phishing emails and can be more difficult to detect.
- Vishing: Vishing attacks use phone calls to trick victims into giving up sensitive information. The caller may pretend to be from a bank, government agency, or other trusted organization.
- Smishing: Smishing attacks use text messages to trick victims into giving up sensitive information. The text message may contain a link to a malicious website or ask you to call a phone number that is controlled by the attacker.
- Pretexting: Pretexting is a type of social engineering attack in which the attacker pretends to be someone else in order to gain your trust. They may call you on the phone, email you, or even meet you in person.
- Baiting: Baiting attacks involve leaving something valuable behind, such as a USB drive or a laptop, in a public place. The victim is then lured into picking up the item and connecting it to their computer, which allows the attacker to install malware or steal data.
- Quid pro quo: Quid pro quo attacks involve offering something of value to the victim in exchange for sensitive information or access to systems. The attacker may offer you a free gift, a discount on a product or service, or even a job.
- Tailgating: Tailgating is a type of social engineering attack in which the attacker follows a victim into a secure area, such as a building or a computer lab. The attacker may then use the victim's access credentials to gain entry to the area.
- Dumpster diving: Dumpster diving is a type of social engineering attack in which the attacker searches through a victim's trash for sensitive information, such as discarded documents or passwords.
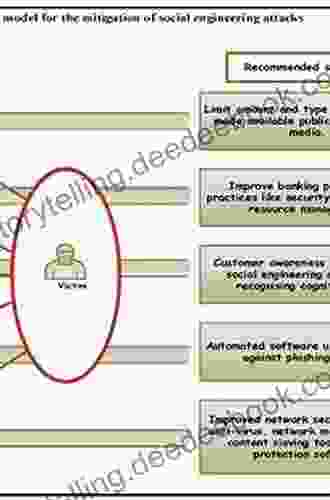
Social Engineering Countermeasures
There are a number of things you can do to protect yourself from social engineering attacks, including:
- Be aware of the different social engineering techniques. The more you know about social engineering, the better equipped you will be to spot and avoid attacks.
- Be suspicious of unsolicited emails, phone calls, and text messages. If you receive an email, phone call, or text message from someone you don't know, be wary of clicking on any links or providing any personal information.
- Never give out your personal information over the phone or email. Legitimate companies will never ask you for your personal information over the phone or email.
- Be careful about what you post on social media. Social media posts can provide attackers with valuable information about you, such as your birthday, your place of work, and your family members.
- Use strong passwords and change them regularly. Strong passwords are at least 12 characters long and include a mix of upper and lowercase letters, numbers, and symbols.
- Install anti-malware software on your computer and keep it up to date. Anti-malware software can help to protect your computer from malware that can be installed by social engineering attacks.
- Educate yourself and your employees about social engineering. The more people who are aware of social engineering, the better equipped they will be to spot and avoid attacks.
Social engineering is a serious threat to organizations today. By understanding the different social engineering techniques and taking steps to protect yourself, you can help to keep your personal information and your organization's data safe.
4 out of 5
| Language | : | English |
| File size | : | 3451 KB |
| Text-to-Speech | : | Enabled |
| Screen Reader | : | Supported |
| Enhanced typesetting | : | Enabled |
| Word Wise | : | Enabled |
| Print length | : | 264 pages |
Do you want to contribute by writing guest posts on this blog?
Please contact us and send us a resume of previous articles that you have written.
 Page
Page Genre
Genre Reader
Reader Bookmark
Bookmark Shelf
Shelf Glossary
Glossary Bibliography
Bibliography Foreword
Foreword Synopsis
Synopsis Annotation
Annotation Codex
Codex Tome
Tome Library card
Library card Narrative
Narrative Biography
Biography Memoir
Memoir Reference
Reference Encyclopedia
Encyclopedia Dictionary
Dictionary Thesaurus
Thesaurus Narrator
Narrator Character
Character Catalog
Catalog Archives
Archives Periodicals
Periodicals Study
Study Research
Research Scholarly
Scholarly Reserve
Reserve Academic
Academic Journals
Journals Reading Room
Reading Room Rare Books
Rare Books Interlibrary
Interlibrary Literacy
Literacy Study Group
Study Group Storytelling
Storytelling Reading List
Reading List Book Club
Book Club Theory
Theory Alan Furst
Alan Furst Nancy Gertner
Nancy Gertner Charles Lowenhaupt
Charles Lowenhaupt Anna Walker
Anna Walker Michael Steen
Michael Steen Walter M X Zimmer
Walter M X Zimmer Grace Divine
Grace Divine Colin Wilson
Colin Wilson Peter Stamatov
Peter Stamatov Athena Steller
Athena Steller Andrew Brel
Andrew Brel Luis Diaz Santana Garza
Luis Diaz Santana Garza Apple Trading And Company
Apple Trading And Company Allen Eskens
Allen Eskens Livi Michael
Livi Michael John Dewey
John Dewey Melissa Payne
Melissa Payne Josh Zimmerman
Josh Zimmerman Rosario Andronaco
Rosario Andronaco Linda Calver
Linda Calver
Light bulbAdvertise smarter! Our strategic ad space ensures maximum exposure. Reserve your spot today!
 David BaldacciFollow ·8.1k
David BaldacciFollow ·8.1k Juan RulfoFollow ·19.8k
Juan RulfoFollow ·19.8k Amir SimmonsFollow ·5.8k
Amir SimmonsFollow ·5.8k Jeremy CookFollow ·8.9k
Jeremy CookFollow ·8.9k Sean TurnerFollow ·11.1k
Sean TurnerFollow ·11.1k Ethan GrayFollow ·9.7k
Ethan GrayFollow ·9.7k Elmer PowellFollow ·12.5k
Elmer PowellFollow ·12.5k Bradley DixonFollow ·13.8k
Bradley DixonFollow ·13.8k

 Howard Blair
Howard BlairClassical Music Themes for Easy Mandolin, Volume One
Classical Music Themes for Easy Mandolin,...

 Paulo Coelho
Paulo CoelhoThe Heretic Tomb: Unraveling the Mysteries of a Lost...
Synopsis In Simon Rose's captivating debut...

 Rodney Parker
Rodney ParkerThe Passionate Friends Annotated Wells: A Deeper...
Unveiling the...

 Ed Cooper
Ed CooperDelicious Stories of Love, Laughs, Lies, and Limoncello...
In the heart of...

 Elmer Powell
Elmer PowellHal Leonard Piano For Kids Songbook: Unleashing the...
Music holds immense...
4 out of 5
| Language | : | English |
| File size | : | 3451 KB |
| Text-to-Speech | : | Enabled |
| Screen Reader | : | Supported |
| Enhanced typesetting | : | Enabled |
| Word Wise | : | Enabled |
| Print length | : | 264 pages |